New Akira ransomware decryptor cracks encryptions keys using GPUs

Security researcher Yohanes Nugroho has released a decryptor for the Linux variant of Akira ransomware, which utilizes GPU power to retrieve the decryption key and unlock files for free.
Nugroho developed the decryptor after being asked for help from a friend, deeming the encrypted system solvable within a week, based on how Akira generates encryption keys using timestamps.
The project ended up taking three weeks due to unforeseen complexities, and the researcher spent $1,200 on GPU resources to crack the encryption key, but eventually, he succeeded.
Using GPUs to brute force keys
Nugroho’s decryptor does not work like a traditional decryption tool where users supply a key to unlock their files.
Instead, it brute-forces encryption keys (unique for each file) by exploiting the fact that the Akira encryptor generates its encryption keys based on the current time (in nanoseconds) as a seed.
An encryption seed is data used with cryptographic functions to generate strong, unpredictable encryption keys. Since the seed influences the key generation, keeping it secret is critical to prevent attackers from recreating encryption or decryption keys through brute force or other cryptographic attacks.
Akira ransomware dynamically generates unique encryption keys for each file using four different timestamp seeds with nanosecond precision and hashes through 1,500 rounds of SHA-256.
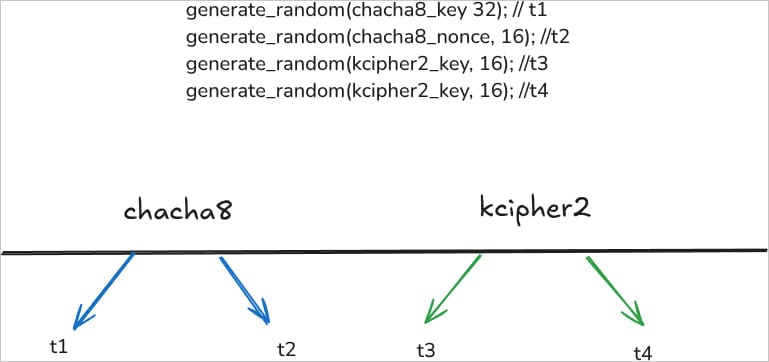
Source: tinyhack.com
These keys are encrypted with RSA-4096 and appended at the end of each encrypted file, so decrypting them without the private key is hard.
The level of timing precision in the timestamps creates over a billion possible values per second, making it difficult to brute force the keys.
Also, Nugroho says that Akira ransomware on Linux encrypts multiple files simultaneously using multi-threading, making it hard to determine the timestamp used and adding further complexity.
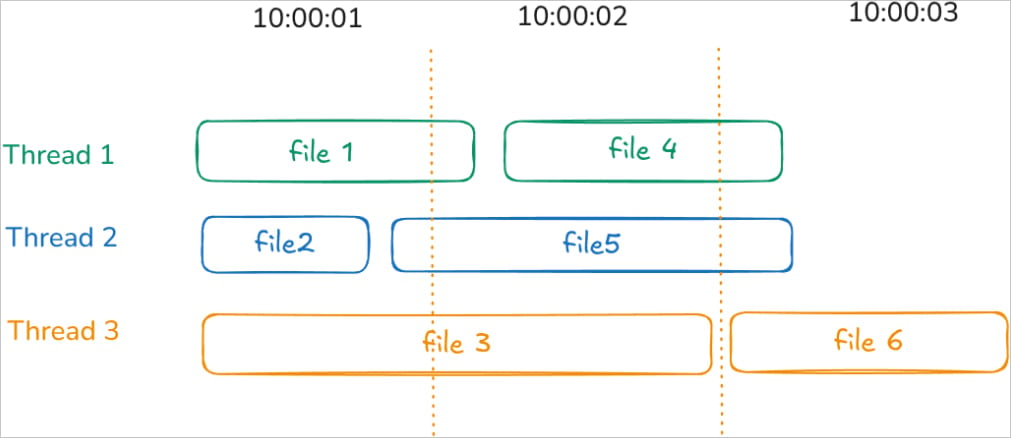
Source: tinyhack.com
The researcher narrowed down the possible timestamps to brute-force by looking at log files shared by his friend. This allowed him to see when the ransomware was executed, the file metadata to estimate the encryption completion times, and produce encryption benchmarks on different hardware to create predictable profiles.
Initial attempts using an RTX 3060 were far too slow, with a ceiling of only 60 million encryption tests per second. Upgrading to an RTC 3090 didn’t help much either.
Eventually, the researcher turned to using RunPod & Vast.ai cloud GPU services that offered enough power at the right price to confirm the effectiveness of his tool.
Specifically, he used sixteen RTX 4090 GPUs to brute-force the decryption key in roughly 10 hours. However, depending on the amount of encrypted files that need recovery, the process may take a couple of days.
The researcher noted in his write-up that GPU experts could still optimize his code, so performance can likely be improved.
Nugroho has made the decryptor available on GitHub, with instructions on how to recover Akira-encrypted files.
As always, when attempting to decrypt files, make a backup of the original encrypted files, as there’s a possibility that files can be corrupted if the wrong decryption key is used.
BleepingComputer has not tested the tool and cannot guarantee its safety or effectiveness, so use it at your own risk.
Source link








